- Back to Home »
- Windows »
- Microsoft Network Monitor
Saturday, November 26, 2011
Microsoft Network Monitor
Overview
Microsoft offers a network diagnostic/monitoring tool that allows you to perform network trouble-shooting tasks. Aptly named Microsoft Network Monitor, this tool collects information from a network’s data stream and displays different types of information, including:- the source address of the computer that sent a frame onto a network
- the destination address of the computer that received the frame
- the protocols used to send the frame
- the data, or portion of the message being sent
- and many others
Capturing
Microsoft Network Monitor collects information using a process known as capturing. You can use this tool to capture statistics on all frames it detects on the network or on a specific subset of frames. In this post, we’ll show you:- where to take a capture,
- how to gather documentation and use a cheat sheet,
- how to customize what information should be captured,
- how to customize the user interface,
- how to make sense of the captured data,
- how to get more information out of the data that’s captured, and
- how to view specific frames in an XML format and in a window by themselves.
Where to take a capture
The decision on where you need to take a capture from will depend on certain conditions like say, the number of machines involved or whether firewalls are in place.For example, if you have two machines, there can be two possible scenarios: 1) when there are no firewalls involved and 2) when there are.
In the first scenario, you can take a trace on either machine. However, in the second scenario, you might want to take a trace on both machines at the same time.
The first trace on the first machine is to determine whether there are any data packets that are being dropped due to existing outbound firewall rules. The trace on the second machine, on the other hand, is to determine whether there are any inbound firewall rules that are preventing data from coming in.
In a real world scenario like the one below, you can take traces on the following locations:
- On the Windows 7 Client’s network interface
- On the internal side of the firewall
- On the external side of the firewall, and
- On the inbound network adapter on the Exchange Server
The trace on the external side of the firewall should be there just in case the firewall has been configured with rules that drop packets which you are not aware of. With these four traces, you can tell whether the packets left the Windows Client, went through the firewall, and entered the Exchange Server.
How to gather documentation and use a cheat sheet
When your network starts to grow and you start having multiple machines (some probably spanning different time zones and continents), you will need to use a cheat sheet to record data regarding issues you encounter along the way.Many of these issues take days or even weeks to resolve and often involve traces with hundreds of thousands packets in them. Oftentimes, you won’t be troubleshooting a single trace in just one troubleshooting session.
So if you don’t keep any documentation, chances are, you’ll forget the details of certain issues in a trace and when it’s time to resume troubleshooting on it, you will be forced to start all over again.
Some of the things you will want to record are:
- the issues themselves
- IP addresses of the machines between which the information you’re looking for is located
- packet numbers you’ve already analyzed or still have to analyze
Let’s assume we have two domain controllers. One domain controller, say DC1, has an IP address of 10.10.10.50. The other domain controller, say DC2, has an IP address of 10.10.10.51.
Let’s also assume that we just mapped a network drive on DC1.
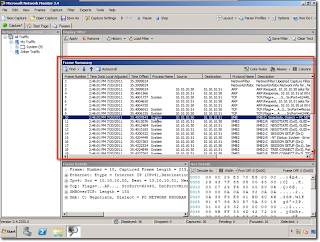
Here’s a typical Frame Summary that includes the traffic generated when the network drive was mapped.
The data packets related to drive mapping are the ones that begin with SMBs (Small Message Block) packets. If, upon mapping the network drive an error occurred and we received an “Access denied” notification, we would have to document the issue.
Your cheat sheet may be a simple Notepad file wherein, for this particular issue, you would jot down the following information:
network drive mapping
error message - access denied
source ip address = 10.10.10.50
destination ip address = 10.10.10.51For more complicated setups, like one where you may be dealing with multiple machines, you may add as many information as you think is necessary. For example, you may want to add a rudimentary graph illustrating what should have happened and where you think the problem might be residing at.
That way, when you get back to this issue in the future, you’ll know what it was all about.
How to customize what information should be captured
You may specify what information should be captured by choosing a Parser Profile. There are five ready-made parser profiles that you can initially choose from. But if you want, you may also create customized parser profiles.The 5 ready-made parser profiles are namely:
Pure - performs no parsing and very limited filtering;
HPC (High Performance Capture) - provides optimized filtering speeds but its filtering capability is limited to TCP and UDP protocols and some protocols related to these two.
Faster Pasing - parses more protocols like: ARP, HTTP, DNS, and NBTNS but doesn’t include SMB and SMB2.
Default - This is the default profile, which parses all the protocols mentioned previously as well as SMB, SMB2, and RPC.
Windows - parses every Windows-based protocol plus SQL. It is considered the heavyweight in terms of parsing cost.
Generally speaking, the more data packet details a packet profile has, the slower the trace will be and the longer it will take to generate its view.
Packet profiles are typically set before you begin your trace. To choose a packet profile, just go to Parser
Profiles > NetworkMonitor Parsers. There you’ll find the parser profiles enumerated above.
How to customize the user interface
Some of you might want to organize your Network Monitor user interface in a particular way so that only the information you’re interested in are shown and so that they are positioned where they can help you work more efficiently.
Some of the things you can do to organize the user interface include:
- docking and un-docking panes
- hiding unwanted panes
- showing the panes you often need,
- getting the default display settings back, and
- changing the layout of the panes to Simple, Diagnostic, Developer, and the default layout
To hide a pane, just click the ‘x’ button on its upper-right corner.
To bring a hidden pane back into view, navigate to the View menu and select the pane you want to show. You will also see a menu item named Restore Default Layout under that menu. Clicking that will restore the layout back to its default settings. You’ll need this if you’ve moved a lot of things around and later on realize you don’t want the new layout after all.
Here’s how the Default Layout looks like.
In addition to the Default Layout, there are also other pre-configured layouts to choose from. To use those layouts, just navigate to the Layout menu and select a layout from there. Notice that the Restore Default Layout can also be selected from that menu.
Here’s how the Diagnostic layout looks like. This layout is normally used if, in addition to other information, you want to see as many frames as possible.
Here’s the Developer layout.
If, after moving panes, removing the ones you don’t like, showing the ones you do, and changing their sizes, you’ve arrived at a customized layout that you really like, you can save that layout for future use. To do that, just click the Save As button.
In the Save As window, give the layout a name (e.g. cap3) and click the Save button.
So the next time you launch Network Monitor, you’ll see that file displayed as a link and ready for use.
How to make sense of the captured data
Using aliasesWhen you start dealing with multiple machines and big traces, that Frame Summary window can be very confusing to look at. It would help you work more efficiently if you could quickly identify the machines involved in a particular process.
For example, it would help if you could quickly determine which machine served as the source machine, i.e. where the command originated from, and which machine served as the destination machine, i.e. where the command was ultimately processed.
One solution is to use aliases. Aliases allow you to turn IP addresses into names that make sense in a particular network capture. For example, you could label one machine as ‘Server’ and another machine as ‘Client’.
In Network Monitor, you can even create an alias list containing all the aliases of all your servers (e.g. Domain Controllers, Exchange Servers, SQL Servers, etc), which you can then use in multiple traces in the future.
To create an alias, click the Aliases menu and select Manage Aliases.
In the Manage aliases window, click New.
Enter the IP address of the machine whom you’d like to assign an alias to. Give it an alias Name. For example, for a machine that initiated a conversation, you can label that Client. Type in a suitable comment. If we use the example in Part 1 of this post, a suitable comment would be “map network drive”. Click OK.
Here’s another sample alias. Here, we created an alias for the server in this particular conversation. Click OK.
You can then click Close if you just intend to use these aliases for one session. Or, alternatively, you could save that list by clicking the Save button. That way, you can load that list in future sessions and apply it to a capture by clicking Open and selecting the list in question.
After closing that window, you’ll then see the newly assigned aliases in the Frame Summary pane (assuming of course the machines in question are there).
Note: When you Open an alias list, you need to click the Apply button under the Aliases menu in order for that list to apply to the capture.
Using PING packets as bookmarksAnother nifty trick you can employ when dealing with really large traces is to use PING packets as bookmarks.
Here’s a sample scenario where you’ll find this particular technique useful. Let’s say you have an Exchange Server and hundreds of Outlook Clients. If one particular Outlook Client is having a problem and is not able to retrieve email from the Exchange Server, how can you quickly focus, in a capture, the interaction between that specific client and the server?
In a typical network environment, you’ll find a cacophony of packets as different machines communicate with one another. Here’s a simplified depiction of such an environment.
PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET
To focus on a particular traffic coming from a particular client, you can use PING. In the sample scenario mentioned earlier, you can go to the Outlook Client, PING the Exchange Server, and then attempt to retrieve email from the server. Once that’s done and you get an error message on your screen, you then PING the server one more time.
PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PING PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PING PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET PACKET
With that, you can then focus on the packets found in between those two PING packets.
How to get more (or less) information out of the data that’s captured
If you look at the Frame Summary pane, you’ll see that there are lots of information in there. You can scroll to the right to see more. But those aren’t the only information that Network Manager is able to gather. You can actually add more information by adding more columns.To do that, just go to the Columns menu and select Choose Columns.
What you’ll see are more or less hundreds of columns which can be added to the Frame Summary.
Just select a column name on the Disabled Columns list and click the Add button. Once a column has been transferred to the Enabled Columns list, you can position the newly added column with respect to the other columns by selecting it and clicking the Move Up or Move Down buttons
After you’re done with all that, click OK.
You’ll then see your newly added column inside the Frame Summary pane. Since you can add columns, you can of course also remove columns. To remove a column, right-click on a column’s heading and, in the context menu that appears, click Remove Column [name of column]. For example, to remove the Time Offset column, right-click on its heading and click Remove Column ‘Time Offset’.
If, after adding, removing, and moving columns, you realize that you’re better off with the default column layout, just click the Columns menu and select Restore Default Column Layout.
Also, in case you want to retain your last column layout. That is, if you want your last column layout to be the same layout on your next Network Monitor session for that capture, make sure the Automatically Save Column Layout (see previous screenshot) is checked.How to view specific frames in a window by themselves or in an XML format
There will be times when you will like to focus on certain frames and concentrate only on the information related to them. You can actually display those frames on a new window by themselves. In the Frame Summary, select the frames you want to focus on, right-click on any of ones you selected, and click View Selected Frame(s) in a New Window.This will then open a separate window containing only those frames you selected. If you click on an individual frame, you’ll see, in the accompanying panes, information related to that particular frame.
Alternatively, you can parse them in an XML file so you can import the information into a different application for whatever your needs might be. To do that, just right-click again on the selected frame or frames and then select Parse Frame as XML.
This is how the data packet would then look like.