Archive for November 2015
Canada Faced Challenge Against Protecting From Cyber-Attacks
An employee monitoring cyber attacks and other security
breaching activity from the hackers such as Financial institutions,
Governments, and big business firms.
Canada is one of the most Cyber security threat affected countries from the
last six months, now Canada dawdle apart from the U.S., Britain and other
developing countries in protecting their own citizen and financial business
institution from cyber attacks in a regular basis, the lack of strategy and
system utility in Canada make more suffer for the government.
In a very productive way the number of cyber attacks increasing
every day. Canada is one of those countries who currently facing the situation
of cyber attacks, and lack of defending the attacks as well. Katherine Thompson
from Canadian Advanced Technology Alliance said, “We’re failing, we’re failing
behind,” CATA is one of the largest private sectors with the high-tech advocacy
group in Canada.
Canada just
recently chosen party leader from the federal election but none of the leader
at that mean time didn’t even discussed about the cyber-security threat
approaching in the country, they didn’t even said that they need to focused
over the development in Cyber Security for the country, Katherine Thompson said
“We cannot continue down the path which currently we are going on right now,”
also she said, “We just went through a very long federal election where not one
of the major party discussed cyber-security.” She told to CBC News Reporter.
Canada Faced Challenge Against Protecting
From Cyber-Attacks
The Canadian
government has invested very low budget in protecting their citizen and other
financial, Business sectors and private institution computer system from cyber
attacks, it is around $245 million investment since 2010 to till date, the
cheap computer equipment and very fewer numbers of equipment supplied to the
government institution.
It has
likewise reserved $142 million throughout the following five years to handle
digital dangers, especially against basic base. Yet, pioneers in Canada’s
policing, IT and digital security parts say the government methodology is
engaged basically on national security dangers and does little to battle the
emotional development in email tricks, online blackmail and ruptures at
corporate PC systems.
Canadians
are likewise to a great extent oblivious about the extent of cybercrimes given
the nation has no focal organization to track online tricks and pernicious
electronic assaults. Besides, are no government laws to constrain organizations
to uncover hacks, security ruptures, robberies of information or cash so the
overall population has deficient learning of which organizations have been
bargained.
“Individuals
having their personality debilitated, or having their PCs tainted, scrapes
secured for payoff, those sorts of things, the normal police headquarters
doesn’t know how to react to that,” says Norm Taylor who drives an official
preparing system for the Canadian Association of Chiefs of Police. “The outcome
is, it’s not being reported. What’s more, the general population is neither
reporting, nor are the police truly doing much in the method for effort to
evaluate those sorts of occurrences,” he says.
The
gathering distinguished “the pressing need to build reporting of digital
violations to police,” and indicated Australia’s ACORN program (Australian
Cybercrime Online Reporting Network) as a model for gathering subject protests
so that police and industry can screen patterns, foil sorted out criminal
gatherings and organize episodes for further examination. The FBI in the U.S.
runs a comparative project called “IC3”, alluding to its Internet Crime Complaint
Center, which a year ago alone got 269,000 objections about cheats, email
tricks and online blackmail. That incorporated around 4,000 protests from
Canada.
How To Become A Pro Gamer – 8 Tips From The Pros
Gaming has come a long way since the days of Pong, Duck Hunt and Pac-Man, when competing meant getting the top score at the local arcade. Electronic sports, or eSports, describes the organized video game competitions (with cash prizes) that are quickly rising in popularity as more gamers become fierce pro competitors.
Now pro gamers are competing around the world — some for winnings in the millions — at events such as the Major League Gaming (MLG) circuit, The International Dota 2 championship and Intel Extreme Masters.

MLG built dedicated arenas across the country to host and stream professional gaming events, and has scouts and communities to find the best untapped players.
Gaming is serious business.
So if you want to be a pro gamer, to make a career out of it, what does it actually take? A lot of dedication, according to pro gamer Ryan “Big Apple Pie” Gresty.
“It takes a lot of your life up, but when you’re in a one-versus-one situation and you know what play to make, you realize all the practice has paid off,” Gresty said. He added that many gamers — or at least himself and the gamers he knows — suffer from “a lack of sleep.”
Rumay “Hafu” Wang began competitive gaming at age 14. Now 23, she evolved her gaming career from team competition, traveling around the world withFnatic, to becoming a full-time streamer on Twitch.
“Streaming is a lot more relaxing,” she said, adding that she plays up to 12 hours a day from the comfort of her home. “You can do it at your own pace, listen to your own music and be your own boss.”
Whether you’re looking to get into team competition or streaming, the following tips can help get you started.
Become a Pro Gamer in 8 Easy Steps
Easy to understand, that is. Playing for a living isn’t all fun and games. It takes time, skill and determination to win in today’s competitive circuits. If you’re up for the challenge, here’s what you need to do:
Pick your game. With a service like Xbox Live, you can practice and compete around the clock both with and against very skilled players. It’s not about randomly finding people to play against. You have to find a game you’re good at and become exceptional at it.
Once you find that game, build your reputation as both a skilled single player and a team player.
Stay motivated. Winning and money are big motivators for pro gamers; so are family and passion. Pro gamer Marcus “ShoNuff2025” Davis has been practicing the latest Call of Duty game, Advanced Warfare.
When asked why he wanted to go pro, Davis said, “First, I want to be the best so my Dad doesn’t think I’m asking for all these games and PC upgrades for nothing. Then I want to have fun doing what I already love doing.”
Practice. Study the best tactics, watch a ton of gameplay and learn how to lose. Even when you lose, you’re practicing, and practice really makes perfect. Tyler “Teepee” Polchow, who was part of the team compLexity (now Evil Geniuses), which won the Call of Duty World Championship in 2014.

“Winning the championship was the pinnacle of my professional gaming career,” Polchow said. To get there, Polchow practiced with his team eight-plus hours a day, live-streamed the games and created other content.
“We were up against the best and had to prove we were better. The grand finals against Team EnvyUs was a quick 3-0 sweep for us, and it was in the last minutes of the third map where we secured the victory,” he said.
“A $100,000 check and the prestige of being a world champion is what all pro gamers strive for, and having that become a reality was one of the most gratifying and relieving feelings.”
Gear up. You need equipment that allows you to properly test your skills against the competition. It might be nice to have the hottest PC, but the most important thing is to choose one with the right performance that suits your lifestyle.
You can get a thin and light gaming notebook to bring to meet up with teammates or make sure practice doesn’t slow down when you travel.
A highly customizable desktop will help ensure that you have the most up-to-date hardware for your ever evolving games. As long as you have an Xbox or PlayStation, you’ll be able to compete.
Join the community. As much as pro gaming is about individual talent, it’s also about the community and being a team player. Before starting, get to know the rules of being part of a particular gaming community.
Find a team. Once you build a reputation as a serious competitor, find a team. If you’re really good, the team will probably find you. If not, try out for teams. MLG has dedicated spots to communicate with other teams and players. There are also communities where you can foster your own team.
Enter tournaments. When you get good enough to compete in singles or with a team, start entering tournaments. Test your skills in as many online and local tournaments as possible. Tournaments happen year round, so you’ll always have a place to compete. The unfortunate news is that no matter how many tournaments you win, your status as a pro gamer is truly only solidified when you win at the pro circuit level. Winning at live events brings you not only respect, but also money. Pro gaming is a legitimate job.
Get sponsored. Today’s pro gamers benefit from sponsors who provide the necessary equipment to compete. If you want to earn a living as a pro gamer, find a way to get sponsored.
“Gaming isn’t just a hobby anymore, it’s a career path and a lifestyle for some people,” Gretsy said. “The dedication and the time put into playing is more than a 9-to-5 job with overtime.”
2014 Call of Duty World Championship image courtesy of Activision.
Daylon Furlough is the author of the Day 8 New Human war book series. He is known in the gaming industry as The Velvet Voice, aka Deacon. He received the Microsoft Xbox MVP for 8 consecutive years and has a love for all things tech, nerd, geek and gaming. He hosts a variety of entertainment events in Dallas, including movie premieres, mobile phone launches, game launches and more. You can visit his website at UNSCRIPTED XBOX.
Tag :
Security
Stealthy GlassRAT Spies on Commercial Targets
A remote
access Trojan used sparingly in targeted attacks has been found after living
under cover for three years, undetected by most security gear.
The RAT,
dubbed GlassRAT, was signed with a certificate belonging to a popular Chinese
software company with hundreds of millions of users worldwide. The RAT was used
to spy on Chinese nationals working in commercial outfits, and could have ties
with other malware campaigns dating back to 2012.
The malware was discovered earlier this year
by researchers at RSA Security during an incident response call. The victim, as
it turned out, was a Chinese national working at a large “multinational
corporation,” RSA said; the victim was not in China. It’s unknown how the
victim was infected, whether via a phishing campaign, drive-by download or some
other means, RSA said.
“There’s not
a whole lot of insight into that beside the specific activity on the
multinational company’s network where there was command and control traffic
from the device via command line,” said Kent Backman, the primary researcher on
the investigation. “There was an actor on the other side investigating the
network that the laptop was on. It seems like an intelligence-gathering tool;
that’s the most likely purpose for this RAT.”
While these
targets were primarily commercial for the purposes of industrial espionage,
some of the command and control infrastructure used by GlassRAT was also used
in previous campaigns against geopolitical targets, likely for some sort of
political espionage.
“We tend to
believe that because the targeting is different, going from geopolitical to
commercial, that we’re probably dealing with a different division of a much
larger hacking organization that showed a few of its cards with respect to
command and control, Backman said.
RSA said it
had to wait several months for a hit on a Yara signature it uploaded to
VirusTotal and other sources before it was able to conclude that the GlassRAT
infrastructure was also used to in attacks against the Philippine and Mongolian
governments but with different malware, Mirage (MirageRAT), magicFire and
PlugX.
“The temporal
overlap window in shared infrastructure was relatively short implying a
possible operational security slip by the actors behind GlassRAT if not
deliberate sharing of infrastructure,” RSA wrote in a report published today.
RSA would not
disclose the company whose certificate was stolen, but did say that it has subsequently
been revoked. The cert was used to sign a dropper for the malware, which
deletes itself after downloading the malware to the compromised machine. RSA
said that the unnamed Beijing-based software company develops one app in
particular that has more than 500 million users, and it’s that application’s
name that the same name used by the malware in the certificate dialog box
during installation.
“We know this
malware was extremely effective on the large multinational corporation,”
Backman said. “It was not detected for years by antivirus, and chances are had
if it were more widely targeted, the chances of escaping AV would have been
less.”
Tag :
Security
5 Must-Use Google Analytics Strategies to Measure SEO Success
You know what they say, “If you can’t measure it, you can’t improve it.” In Search Engine Optimization measurement is critical to success. Sure, keyword rankings are a great measure of SEO. More keywords ranking higher means more traffic, right? But, reporting solely on keywords devalues the marketer’s role and doesn’t paint the full picture of why SEO is important to the organization. Going beyond keyword rankings allows marketing teams to showcase what really matters: how organic search brings revenue and profit to the business. Thankfully, one of the best tools for measuring SEO is freely available, and probably already installed on your website – Google Analytics!
Although every business is unique and every website has different metrics that matter, this post is a universal list of 5 ways to use Google Analytics to report the success of your businesses SEO efforts.
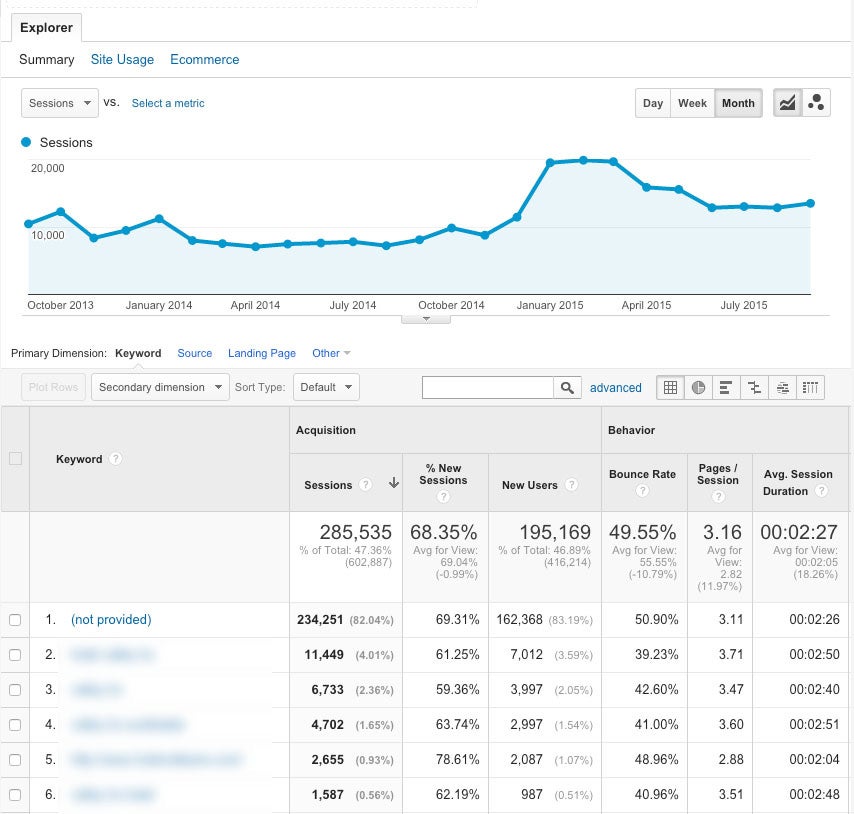
1. How to View Only Organic Search Traffic
This one might seem obvious. I’m always surprised at how many companies see a decline in overall website traffic and immediately jump to the conclusion that the traffic loss is due to a decline in organic search traffic. Many times digging a little deeper can actually reveal that organic traffic is up while other traffic sources are down which is resulting in the overall traffic decline.
The first step in looking at Organic Search traffic over time is to open yourChannel Grouping report which can be found by clicking Acquisition > All Traffic > Channels. There you will see traffic sources segmented by channel.
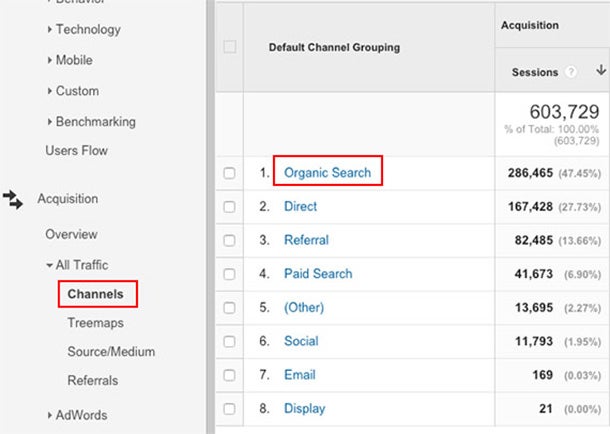
Clicking on the “Organic Search” channel will give you a more detailed report which includes only organic search traffic metrics.
Click to Enlarge+
This report will be the Swiss Army Knife to your SEO reporting. From this report you can determine things such as the top landing pages for search traffic, keywords driving the most traffic, which search engines are sending the most traffic, top exit pages and much, much more.
2. How to Measure The Quality of SEO Traffic
A lot of times I hear that “quality” is subjective, so you can’t really measure it. I don’t believe this to be true and in fact, I’d say there are a lot of ways to measure the quality of any traffic source, not just search.
The most common report I use to measure an improvement or decline in the quality of search traffic is the Assisted Conversions report (Conversions > Multi-Channel Funnels > Assisted Conversions). With this report active I like to start by setting the date range to ‘Last month’ and comparing it to ‘Previous period’. What you’re left with is a month-to-month comparison of conversions directly from search, or in the event of multiple visits to the site, conversions where search played a role but is not directly attributed with the conversion (ie: the visitor found the company through search, but returned directly and converted).
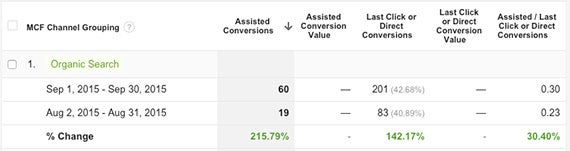
Use this report to look for a decline or improvement in conversions from search traffic. If businesses notice a decline in conversions from search, yet overall search traffic is steady, it’s easy to determine that the traffic coming from search is not qualified or of a very high quality.
Likewise, if you begin focusing on a more refined set of keywords and see an improvement in conversions from search traffic, you can say your SEO traffic quality is improving.
3. Assigning Dollar Values to Organic Traffic
This is a strategy I use for businesses who are looking for a more traditional way to understand the value SEO is bringing to their business beyond improvements in traffic, visibility and conversions by assigning a dollar value to their organic traffic results. To assign a total dollar value to a sites organic traffic, I compare how much the keywords would cost if purchased in a Google AdWords campaign.
Note: For this strategy to work you will need access to a Google AdWords account, and your Analytics will need to be synced with your Search Console account.
To find a sites keyword search phrases and queries, navigate to Acquisition > Search Engine Optimization > Queries.
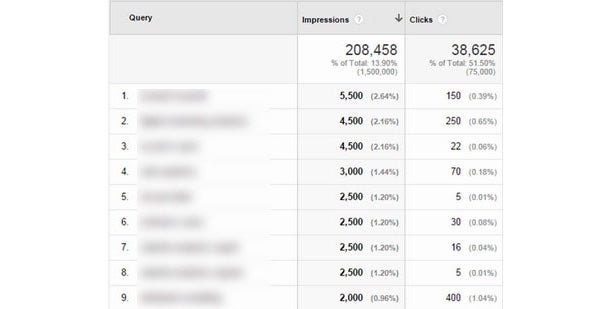
With this report pulled up, open your AdWords account in a new tab and clickTools > Keyword Planner. For this strategy we want to choose “Get search volume data and trends”, enter the top keywords from your Google Analytics Queries report, and click “Get search volume.” On the next screen click “Keyword Ideas.” Each keyword you’ve entered will have a Suggested Bid amount which is an estimate of what advertisers are currently paying per click for each keyword listed.
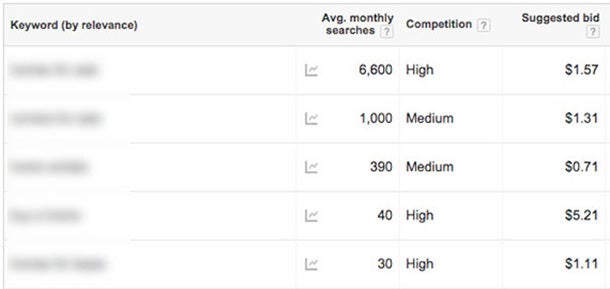
In a spreadsheet I will list all known keywords driving traffic to the website, the amount of click-throughs from each keyword, and the estimated cost-per-click. The final column in the spreadsheet is the sum of the estimated cost per click multiplied by the amount of clicks, resulting in the total organic traffic value per keyword.
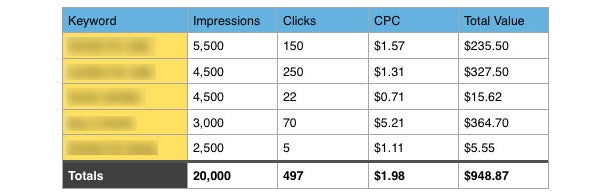
This is a great strategy to visualize what kind of dollars and cents a businesses SEO strategy is saving them on traffic they would otherwise have to pay for.
4. Identifying Slow Loading Page Times
The need to optimize page load times is one item that is majorly overlooked by many SEO’s. In addition to how slow loading pages affect the user experience, page speed has become a major factor in search rankings. That’s why I always suggest that if a business is investing time and money in SEO and keyword rankings, don’t blow it by overlooking a slow loading website.
While we aren’t going to talk about how to make a website load faster, I want to look at how to identify slow loading pages and measure their impact on conversion rates.
To measure page load times on a page-by-page basis navigate to Behavior > Site Speed > Page Timings. I like to set the middle column to ‘Avg. Page Load Time’ and the right column to ‘% Exit’. I also will typically add a ‘Secondary Dimension’ of Medium, and filter down to show only organic traffic.
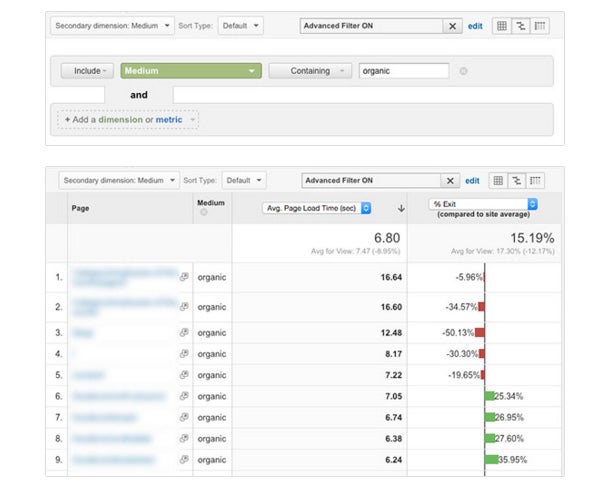
What this report shows us in the top most row is the average page load time site wide, and the average exit percentage (where a visitor decides to leave the site) on a page-by-page basis. It’s also fairly easy to see in this report that as our page load time surpasses our site wide average, our exit percentages begin to skyrocket.
As an SEO, what I will do is bring this report to the site developers and ask them to do everything they can to optimize page load times. Once page load times have been improved, I will run this same report and compare it to the old data to show how much additional search traffic we’ve retained, and most likely converted due to the improvement in page load times.
5. Create Your Own SEO Dashboard
Sometimes all it takes to move a client or boss from a skeptic to a believer in your work is how the data is presented. It’s easy as an internet marketer – or more specifically an SEO – to over explain ourselves, or lean on hard-to-grasp metrics. Sometimes all the client wants to see is bar graphs, pie charts and other less intimidating forms of measurement.
The best way I’ve found to present Google Analytics and SEO data is through the built in Dashboard interface. A Dashboard is essentially a series of Widgets which pull all of the individual reports into a single view which is easy to access, share, and print. The bonus to having an easily presentable PDF of SEO metrics is the fact that having this dashboard will also cut down on your time spent reviewing Analytics letting you focus on actually doing the SEO work.
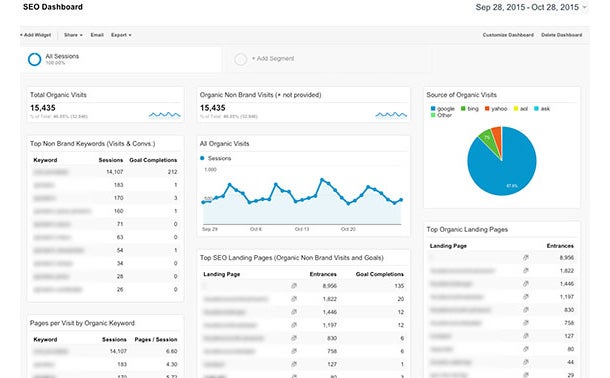
If you want to skip the details and import my dashboard you can do that, otherwise click on Dashboards > + New Dashboard.
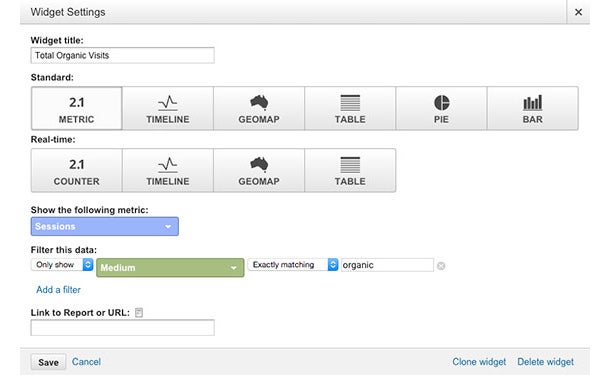
The first widget I always set up is a simple counter to measure total visits to the site from organic search. Click on “+ Add Widget”, and title it “Total Organic Visits”. For this widget I usually stick with the ‘Metric’ display. Under “Show the following metric:” select ‘Sessions’. Since we only want to see traffic from organic search we need to create a filter. Under “Filter this data:” select Only show > Medium > Exactly matching > organic.
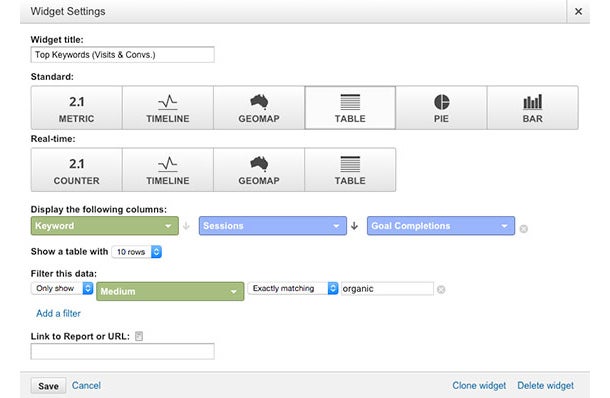
Let’s set up one more widget. My second favorite widget measures keyword phrases sorted by the amount of sessions and goal completions resulting from the respective keyword. Let’s add a new widget like before, but this time let’s set our display as “Table”. Under “Display the following columns:”, choose Keyword > Sessions > Goal Completions. We also want to apply the same organic traffic filter as our first widget.
I like tailor these reports to the specific client, but other widgets I usually create include:
- All Organic Visits Over Time (Timeline)
- Top SEO Landing Pages
- Top Organic Keywords & % of New Visits
- Pages per Visit by Organic Keyword
- Most Successful Keywords by Goal Completions
Turning a Challenge Into a Strength
By far, the single most challenging aspect of being an SEO is being able to effectively articulate the value you are bringing to a business. It’s easy for an SEO to show another SEO how his or her numbers are improving, but being able to quantify your work from a traffic and revenue stand point to a client or your boss is essential to earning and retaining business. If a client doesn’t understand what that check they’re writing is doing for their business, it won’t be long before they stop writing that check.
Pay attention to what metrics resonate with your client or boss and find a creative way to represent this data in your monthly SEO reports. For extra brownie points, when clients or bosses have shared access to the Analytics I always make a point to walk them through the custom dashboards showing them exactly what each widget is tracking and why it’s important to measure. Being able to educate your client on your process helps them appreciate the value you’re bringing to their business and view you as an asset to their future traffic goals.
Iranian Hackers Attacked State Department From Facebook Account
Iranian hackers working under Iranian Government, hackers in October attack social media accounts of State Department employee. Neither the victim nor the US government has got information regarding the breach.
Hackers working for the Iranian government supposedly broke into the online networking records of a few individuals at the State Department a month ago. Also, neither the casualties nor the US government thought about it until Facebook alarmed them to the break. These interruptions are a piece of a greater cyberespionage battle, as per a report in the US blog post that refers to unknown government authorities.
It’s vague how harming or fruitful the hacking effort has been, however these assaults affirm that Iran is dynamic in the internet, and that the US government, and its workers, are badly arranged to counter or counteract such assaults. State Department representatives didn’t even notice the assaults until Facebook communicated something specific informing them they had been casualties of a cyberattack.
Iranian Hackers Attacked State Department From Facebook Account
“We trust your Facebook account and your other online records may be the objective of assaults by state-supported on-screen characters,” the caution expressed. The State Department did not answer a solicitation for input, and Facebook likewise declined to remark. In any case, a year ago, private security analysts say, Iranians started utilizing cyberattacks for reconnaissance, instead of for annihilation and interruption.

Starting in May 2014, scientists discovered proof that Iranian programmers were focusing on Iranian nonconformists, and later arrangement creators, senior military work force and resistance temporary workers in the United States, England and Israel, as indicated by a report by iSight Partners, a PC insight firm in Dallas.
Generally, other researchers said, the assaults were fundamental “lance phishing” endeavors, in which aggressors attempted to draw their casualties into tapping on a malevolent connection, for this situation by mimicking individuals from the news media. Iranian programmers were fruitful in more than a quarter of their endeavors.
The quantity of such assaults came to a peak in May only in front of the atomic talks in Vienna in July coming to more than 1,500 endeavors, as indicated by scientists at Checkpoint, the Israeli cybersecurity organization. Be that as it may, a source near the occurrence, who requested that talk secretly given the affectability of the matter, affirmed The New York Times report. Recently, Motherboard reported that programmers with connections to the Iranian government were included in a progression of endeavors to bargain the Gmail records of columnists and activists.
For the last couple of years, US government authorities and private security firms alike have been cautioning that Iran has been getting more dynamic and complex in its cyberattack endeavors, in spite of the fact that there’s minimal hard confirmation of what, precisely, those endeavors involve. That crusade focused on diaspora Iranians and the activists working with them.
Tag :
Security
How To Crack Windows 7,8,10 Password
Today most of our users are using windows as operating system in their laptop and computer and as we all know that windows has lots of features it and also lots of vulnerabilities. And also in windows some time you forgot your user account password and at that time you don’t have access to your files and folders. You only get stuck at the login screen. So at that time you have one option to install the operating system again, but it leads to loss of data which not seems to be a better choice. Yes you can do this by your own. You just need to follow some of the simple steps that i have discussed below and after that you can easily reset your forgotten password.Learn How To Crack/Hack Windows 7,8,10 Password
This tutorial is just for educational purpose. All contents of this article are provided for information and educational purposes only.
How To Crack Windows 7,8,10 Password
This method actually works on boot screen that is only way to access the internal settings of windows that will now Hack Windows Password for you. You just need a windows bootable pendrive that will allows you to reset the settings of current windows. Now just follow some simple steps discussed below to proceed.
Steps To Crack Windows XP,7,8,8.1, Windows 10 Password:
- First of all create a bootable pendrive/CD/DVD of current windows (e.g. we use windows 8.1).
- Now insert that bootable media in your computer and restart your computer.
- Now as soon as computer starts click on F12 button to select the boot able media to boot, or you can change the priority order of boot able device by going into BIOS settings.
- Now when you media boots then it will ask you for press any key to boot, just press any key of your keyboard.
- Now windows starts loading, there select language and then click on next option.
- Now select Repair Your Computer and after that select troubleshoot option there.
- Now select Microsoft Diagnostics & Recovery Tool and then click on exit.
- Now there at next option select your OS type and then Locksmith and click on next option there.
- Now there you can select any of the account whose password you want to change.
- Select any of account and then change password and there type new password and then confirm password.
- Now click on finish button and restart your computer.
- Thats it you are done when you come to login screen, just enter the password you have set and you will get logged in.
So above is all about Crack Windows 10 Password. By this simple method you can easily reset password of any of account in any version of windows just with your magical media device and your magical brain that you will use to implement this method. Hope you like the discussion, don’t forget to share it with your friends and leave a comment below if you need any help from us.
Cybercrime in India Lost Rs.16,000 Average 11.3 Million Attacks
Norton by Symantec published its Indian Search report on Cybercrime, it found online credit card details are more vulnerability to be stolen by the hackers from the users Laptop, Smartphone or any used ATM machine.
Today Norton by Symantec which is also a part of external Google, which discharged its India discoveries from the Norton Cybersecurity Insights Report, which reveals insight into the truths of online wrongdoing and the individual impact it has on buyers. In the previous year, 48 percent of India’s online populace or roughly 113 million Indians were influenced by online wrongdoing,” said Ritesh Chopra, Country Manager, India, Norton by Symantec.
The report found that 60 percent of individuals stress over encountering cybercrime. Interestingly, 54 percent of Indians trust it’s more probable their Visa data will be stolen online than from their wallet and one in two 52 percent Indians have either by and by experienced Mastercard misrepresentation or know somebody who has. Chora said: “Despite the fact that Millennials have been inundated in online innovation the vast majority of their lives, they are more foolhardy from numerous points of view with one and only in four trusting they have most obligation when an online wrongdoing happens,”
Cybercrime in India Lost Rs.16,000 Average 11.3 Million Attacks
Two in three Indian 66 percent shoppers think utilizing open Wi-Fi is more dangerous than utilizing an open restroom. “Our discoveries uncover that customer reservations are in fact grounded in actuality. Near two in three 64 percent think putting away their charge card and keeping money data in the cloud is more hazardous than not wearing a safety belt. While Millennials, conceived in the computerized time, regularly laugh in the face of any potential risk with 31 percent confessing to sharing passwords and other unsafe online conduct.
“Notwithstanding the risk of cybercrime in India, it hasn’t prompted boundless appropriation of straightforward assurance measures to protect data on the web, with right around one in four Indians sharing passwords as a typical practice,” he said. Eight in 10 80 percent say that it is more hazardous to impart their email secret word to a companion than their auto for a day. Four in 10 Millennials trust that they aren’t “sufficiently fascinating” to be an objective of online wrongdoing.
Millennial Indians More Reckless In Their Online Behavior. Indian customers influenced by cybercrime lost overall 29.6 hours contrasted with a normal of 21 hours over the 17 nations overviewed. As a general rule be that as it may, more than seven in 10 Millennials in India have ever encountered a type of cybercrime; with consistently Millennial (54 percent) encountering it in the most recent 12 months alone. Yet, with regards to wholesale fraud, just a large portion of the Millennials concur that it is more probable than at any other time.
On top of this misfortune, cybercrime takes a genuine enthusiastic toll with about portion of purchasers encountering cybercrime in India feeling enraged in the wake of being influenced by cybercrime. Who best the rundown of those most mindful of online security hones in India? Children of post war America a gathering regularly thought to be less educated report more secure online propensities than Millennials. At 32 percent, twice the same number of Indians driven for the most part by Millennials report expressly having their cell phone stolen contrasted with the worldwide normal of 15 percent.
The Essential Skills to Becoming a Master Hacker
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"
As the hacker is among the most skilled information technology disciplines, it requires a wide knowledge of IT technologies and techniques. To truly be a great hacker, one must master many skills. Don't be discouraged if you don't have all the skills I list here, but rather use this list as a starting ground for what you need to study and master in the near future.
This is my overview list of required skills to enter the pantheon of this elite IT profession. I've broken the skills into three categories to help you go from one rung to the other more easily—fundamental, intermediate, and intangible skills—and have included links to related articles on Null Byte for you to get acquainted with.
The Fundamental Skills
These are the basics that every hacker should know before even trying to hack. Once you have a good grasp on everything in this section, you can move into the intermediary level.
1. Basic Computer Skills
It probably goes without saying that to become a hacker you need some basic computer skills. These skills go beyond the ability to create a Word document or cruise the Internet. You need to be able to use the command line in Windows, edit the registry, and set up your networking parameters.
Many of these basic skills can be acquired in a basic computer skills course like A+.
2. Networking Skills
You need to understand the basics of networking, such as the following.
- DHCP
- NAT
- Subnetting
- IPv4
- IPv6
- Public v Private IP
- DNS
- Routers and switches
- VLANs
- OSI model
- MAC addressing
- ARP
As we are often exploiting these technologies, the better you understand how they work, the more successful you will be. Note that I did not write the two guides below, but they are very informative and cover some of the networking basics mentioned above.
3. Linux Skills
It is extremely critical to develop Linux skills to become a hacker. Nearly all the tools we use as a hacker are developed for Linux and Linux gives us capabilities that we don't have using Windows.
If you need to improve your Linux skills, or you're just getting started with Linux, check out my Linux series for beginners below.
4. Wireshark or Tcpdump
Wireshark is the most widely used sniffer/protocol analyzer, while tcpdump is a command line sniffer/protocol analyzer. Both can be extraordinarily useful in analyzing TCP/IP traffic and attacks.
5. Virtualization
You need to become proficient in using one of the virtualization software packages such as VirtualBox or VMWare Workstation. Ideally, you need a safe environment to practice your hacks before you take them out in real world. A virtual environment provides you a safe environment to test and refine your hacks before going live with them.
6. Security Concepts & Technologies
A good hacker understands security concepts and technologies. The only way to overcome the roadblocks established by the security admins is to be familiar with them. The hacker must understand such things as PKI (public key infrastructure), SSL (secure sockets layer), IDS (intrusion detection system), firewalls, etc.
The beginner hacker can acquire many of these skills in a basic security course such as Security+.
7. Wireless Technologies
In order to be able to hack wireless, you must first understand how it works. Things like the encryption algorithms (WEP, WPA, WPA2), the four-way handshake, and WPS. In addition, understanding such as things as the protocol for connection and authentication and the legal constraints on wireless technologies.
To get started, check out my guide below on getting started with wireless terms and technologies, then read our collection of Wi-Fi hacking guides for further information on each kind of encryption algorithms and for examples of how each hack works.
The Intermediate Skills
This is where things get interesting, and where you really start to get a feel for your capabilities as a hacker. Knowing all of these will allow you to advance to more intuitive hacks where you are calling all the shots—not some other hacker.
8. Scripting
Without scripting skills, the hacker will be relegated to using other hackers' tools. This limits your effectiveness. Every day a new tool is in existence loses effectiveness as security admins come up with defenses.
To develop your own unique tools, you will need to become proficient at least in one of the scripting languages including the BASH shell. These should include one of Perl, Python, or Ruby.
9. Database Skills
If you want to be able to proficiently hack databases, you will need to understand databases and how they work. This includes the SQL language. I would also recommend the mastery of one of the major DBMS's such SQL Server, Oracle, or MySQL.
10. Web Applications
Web applications are probably the most fertile ground for hackers in recent years. The more you understand about how web applications work and the databases behind them, the more successful you will be. In addition, you will likely need to build your own website for phishing and other nefarious purposes.
11. Forensics
To become good hacker, you must not be caught! You can't become a pro hacker sitting in a prison cell for 5 years. The more you know about digital forensics, the better you can become at avoiding and evading detection.
12. Advanced TCP/IP
The beginner hacker must understand TCP/IP basics, but to rise to the intermediate level, you must understand in intimate details the TCP/IP protocol stack and fields. These include how each of the fields (flags, window, df, tos, seq, ack, etc.) in both the TCP and IP packet can be manipulated and used against the victim system to enable MitM attacks, among other things.
13. Cryptography
Although one doesn't need to be a cryptographer to be a good hacker, the more you understand the strengths and weaknesses of each cryptographic algorithm, the better the chances of defeating it. In addition, cryptography can used by the hacker to hide their activities and evade detection.
14. Reverse Engineering
Reverse engineering enables you to open a piece of malware and re-build it with additional features and capabilities. Just like in software engineering, no one builds a new application from scratch. Nearly every new exploit or malware uses components from other existing malware.
In addition, reverse engineering enables the hacker to take an existing exploit and change its signature so that it can fly past IDS and AV detection.
The Intangible Skills
Along with all these computer skills, the successful hacker must have some intangible skills. These include the following.
15. Think Creatively
There is ALWAYS a way to hack a system and many ways to accomplish it. A good hacker can think creatively of multiple approaches to the same hack.
16. Problem-Solving Skills
A hacker is always coming up against seemingly unsolvable problems. This requires that the hacker be accustomed to thinking analytically and solving problems. This often demands that the hacker diagnose accurately what is wrong and then break the problem down into separate components. This is one of those abilities that comes with many hours of practice.
17. Persistence
A hacker must be persistent. If you fail at first, try again. If that fails, come up with a new approach and try again. It is only with a persistence that you will be able to hack the most secured systems.
I hope this gives you some guidelines as to what one needs to study and master to ascend to the intermediate level of hacking. In a future article, I'll discuss what you need to master to ascend into the advanced or master hacker level, so keep coming back, my novice hackers!